My two last posts (about the GI update) used the GOLD IMAGE (link post#1, and post#2), where we basically deploy a patched image of the desired version. But this is different when we use the Release Update patch. Below I will describe how to do this, covering all the steps, using the silent install (easily adapted for automation), and with Zero-Downtime Oracle Grid Infrastructure Patching – ZDOGIP (that can easily bypassed if you want).
Tag Archives: MAA
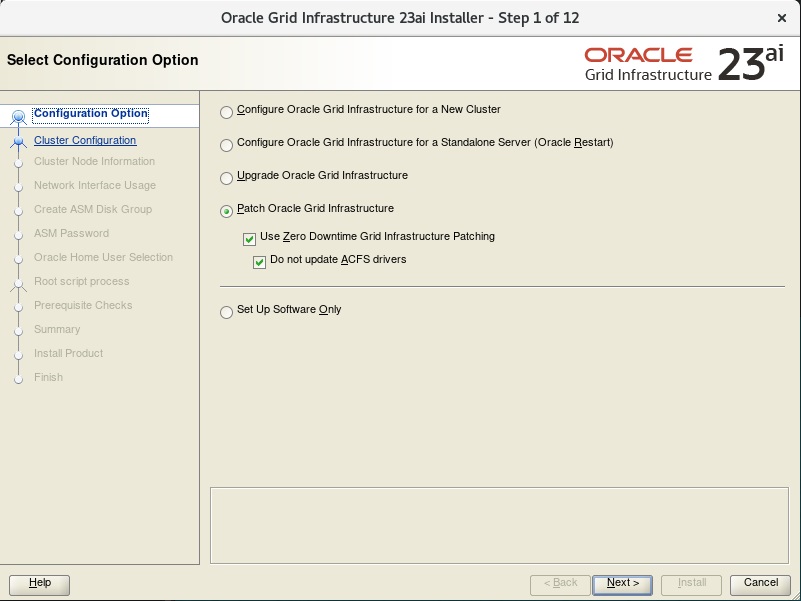
23ai, Zero-Downtime Oracle Grid Infrastructure Patching – GOLD IMAGE with Silent Install
My previous post was about the Zero-Downtime Oracle Grid Infrastructure Patching (ZDOGIP) for 23ai using the gold image. In that case, I used the GUI interface to do the installation and patch, but as you know, this is not good for the automation process. So, here in this post, I will describe how to do the same operation using the silent mode for the installation. I will show what parameters you need to set in the response file and all the other steps.
Important details
The focus of this post is to show how to do the same process as my previous post using the silent mode. I will not “prove” (like I made in the last one) that databases continue to receive inserts or details about the AFD/ACFS drivers not being updated. I really recommend that you read my previous post to understand all of these details. Here I will show how to do in silent mode what I made in the previous post.
23ai, Zero-Downtime Oracle Grid Infrastructure Patching – GOLD IMAGE
As you know, the 23ai was released for Cloud and Engineered Systems (Exadata and ExaCC) first, I already explored these in previous posts as well. And since the patches already started to be released, now with the patch for 23.6, we can re-test the feature Zero-Downtime Oracle Grid Infrastructure Patching (ZDOGIP). The steps here are not specific to the Exadata version and can be used for any 23ai version.
I already demonstrated how to use it for 21c (using graphical, and silent mode) and the same can be done for 19c as well.
But now, I will show how to do for 23ai, and this post includes:
- Install the Grid Infrastructure 23.6.0.24.10, using the Gold Image
- Upgrade the GI from 23.5.0.24.07 to 23.6.0.24.10 using the Zero-Downtime Oracle Grid Infrastructure Patching
This will be done while the database is running to show that we can patch the GI without downtime. I will show how to do this:
21c, Zero-Downtime Oracle Grid Infrastructure Patching – Silent Mode
Recently I made two posts about the process for patch/upgrading your 21 Grid Infrastructure (GI) while the databases continue to be running. The first post shows how to do this using the GUI interface, and the second one show more details about the process for AFD/ACFS Kernel Driver Update. But here in this post, I will show how to do the Zero-Downtime Patch (zeroDowntimeGIPatching – ZDGIP) in silent mode.
This way to do the patch is important because allows you to automatize it. You can create your own script and call it (using Ansible, Puppet, Chief, etc.) to upgrade your servers (or farms) remotely.
Current Environment
The current environment is the same of the first post:
- OEL 8.4 Kernel 5.4.17-2102.201.3.el8uek.x86_64.
- Oracle GI 21c, version 21.3 with no one-off or patches installed.
- Oracle Database 21c, RU 21.5 (with OCW 21.5).
- TFA version is 21.4 (last available in March 2022).
- Nodes are not using Transparent HugePages.
- Is a RAC installation, with two nodes.
You can see the output for the info above in this txt file.
And I will apply the same RU 21.5 (21.5.0.0.220118) for GI which is patch 33531909.
Patch Process
The patch process is almost the same as the first post, the main change is the response file and the way to call the gridSetup.sh. So, for this reason, I recommend for you read the first (and second) post. Below you will see a quick review of previous steps and a focus on the new
21c, updateosfiles after Grid Infrastructure Patch
Recently I made one post about how to use the new feature -zeroDowntimeGIPatching when patching the Grid Infrastructure for 21c. It is a new feature/option that allows your database continues to be running while the grid is patched. You can see my post here. But during that post I talked about the usage of -updateosfiles when calling the rootcrs.sh and want to clarify some details and provide better examples.
Current environment
For this post, my environment is:
- OEL 8.4 Kernel 5.4.17-2102.201.3.el8uek.x86_64.
- Oracle GI 21c, version 21.5.
- Is a RAC installation, with two nodes.
The GI was upgraded from 21.3 to 21.5 as demonstrated in my post.
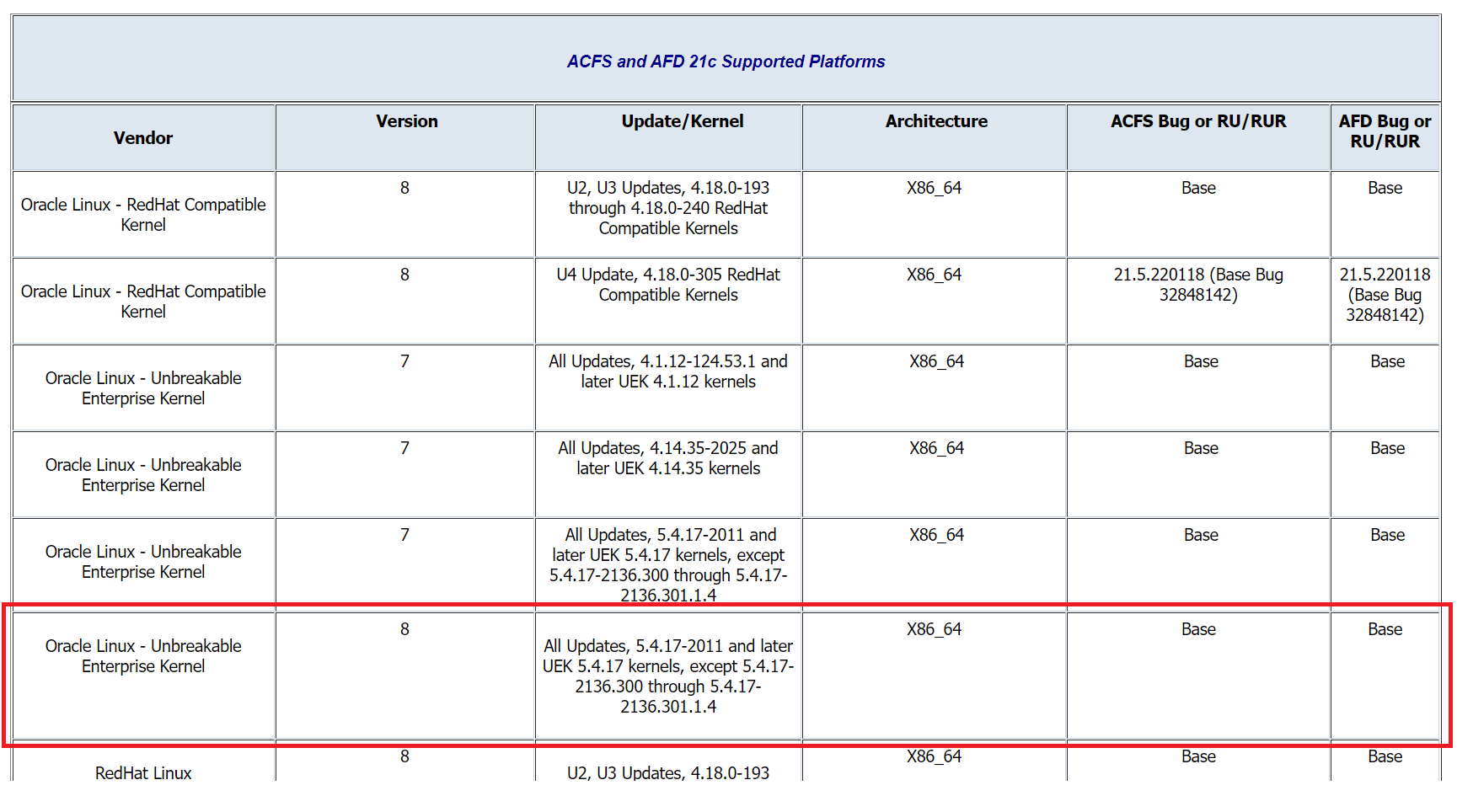
Compatibility Matrix
Before you think about upgrading the ACFS/AFD drivers you need to check if they are compatible with the version or kernel that you are running. The only place to check this is the MOS note ACFS Support On OS Platforms (Certification Matrix). (Doc ID 1369107.1). On that note, you will see tables for each major version (18c, 19c, 21c), and you can see the versions of Linux Version and Kernel versions that are compatible. Below is marked for OEL 8:
And you can see that my version of Linux Kernel is compatible. If your version is not compatible, not update the ACFS/AFD kernel drivers.
21c, Zero-Downtime Oracle Grid Infrastructure Patching
Oracle 21c delivered a lot of new features and for Grid infrastructure one of the most interesting is the zero-downtime patch (zeroDowntimeGIPatching). This basically allows your database continues to be running while you patch/upgrade your GI. The official doc can be seen here. Let’s say that is an evolution of the Out of Place (OOP) patch for GI.
In this post I will show how to do that, but some details before starting:
- This post shows how to do the zero-downtime patch using GUI mode.
- I will do another post showing how to do in silent mode the same procedure. So, it can be automatized.
- In a third post, I will detail how the zero-downtime works behind the scenes and will discuss some logs.
Oracle Engineered Systems since 2010
Recently I made a tweet about a new project with Oracle Engineered System (X9M) that remembered me about what I made with these systems until now. So, this opened the opportunity to tell my background and history until now working with these systems. Is not a show-off of ego boost post.
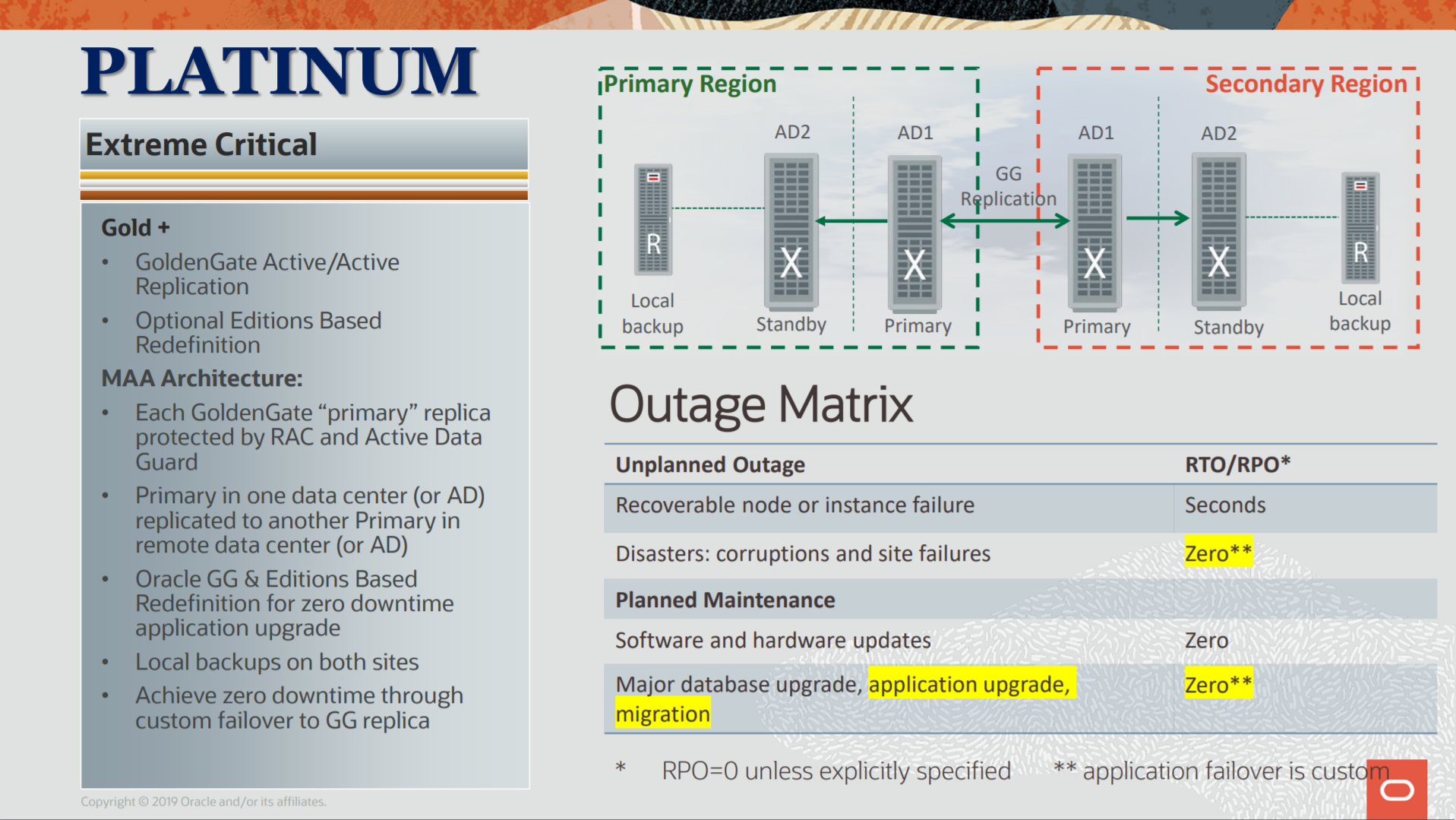
ZDLRA + MAA, Protection for Platinum Architecture
The Platinum architecture is the last defined at MAA references and is the highest level of protection that you can achieve for MAA. It goes beyond the Gold protection (that I explained in my previous post) and you can have application continuity even version upgrade for your database.
The image above was taken from https://www.oracle.com/a/tech/docs/maa-overview-onpremise-2019.pdf
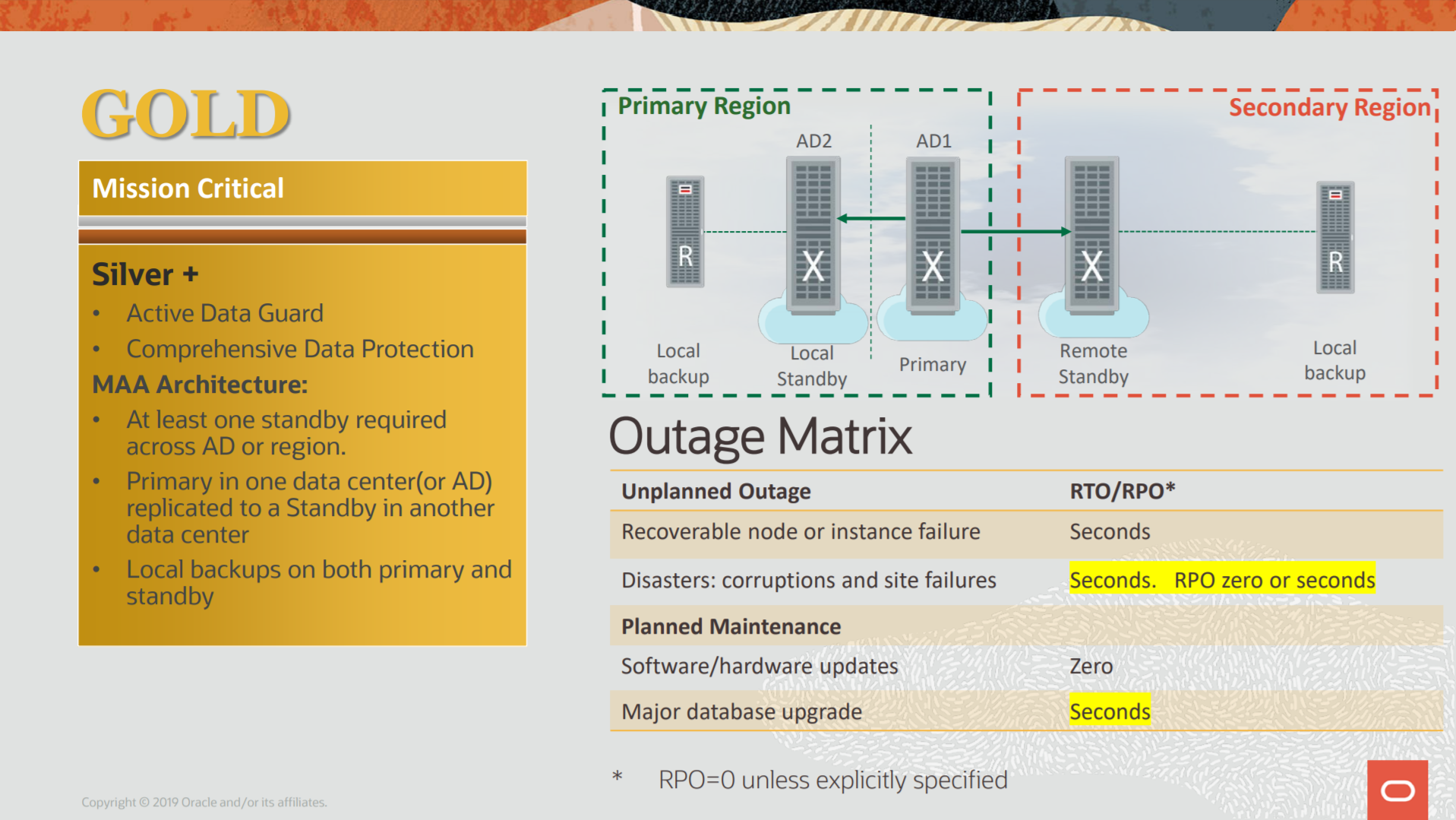
ZDLRA + MAA, Protection for Gold Architecture
The Gold architecture for MAA is used to emphasis the application continuity. All the possible outages (planned or no) are protected by Oracle features. Here we are one step further and start to design using multi-site architecture. Data Guard, RAC, Oracle Clusterware, everything is there. But even with these, ZDLRA is still needed to allow complete protection.
The image above taken from https://www.oracle.com/a/tech/docs/maa-overview-onpremise-2019.pdf.
With the MAA references, we have the blueprints and highlights how to protect them since the standalone/single instance until the multiple site database. But for Gold we are beyond RPO and RTO, they are important but application continuity and data continuity join to complete the whole picture.
ZDLRA + MAA, Protection for Silver Architecture
The MAA defined Silver architecture for database environments that use (or need) high availability to survive for outages. The idea is having more than one single instance running, and to do that, it relies on Oracle Clusterware and Engineered Systems to mitigate the single point of failure. But is not just a database that gains with this, the Silver architecture is the first step to have application continuity. And again, ZDLRA is there since the beginning.
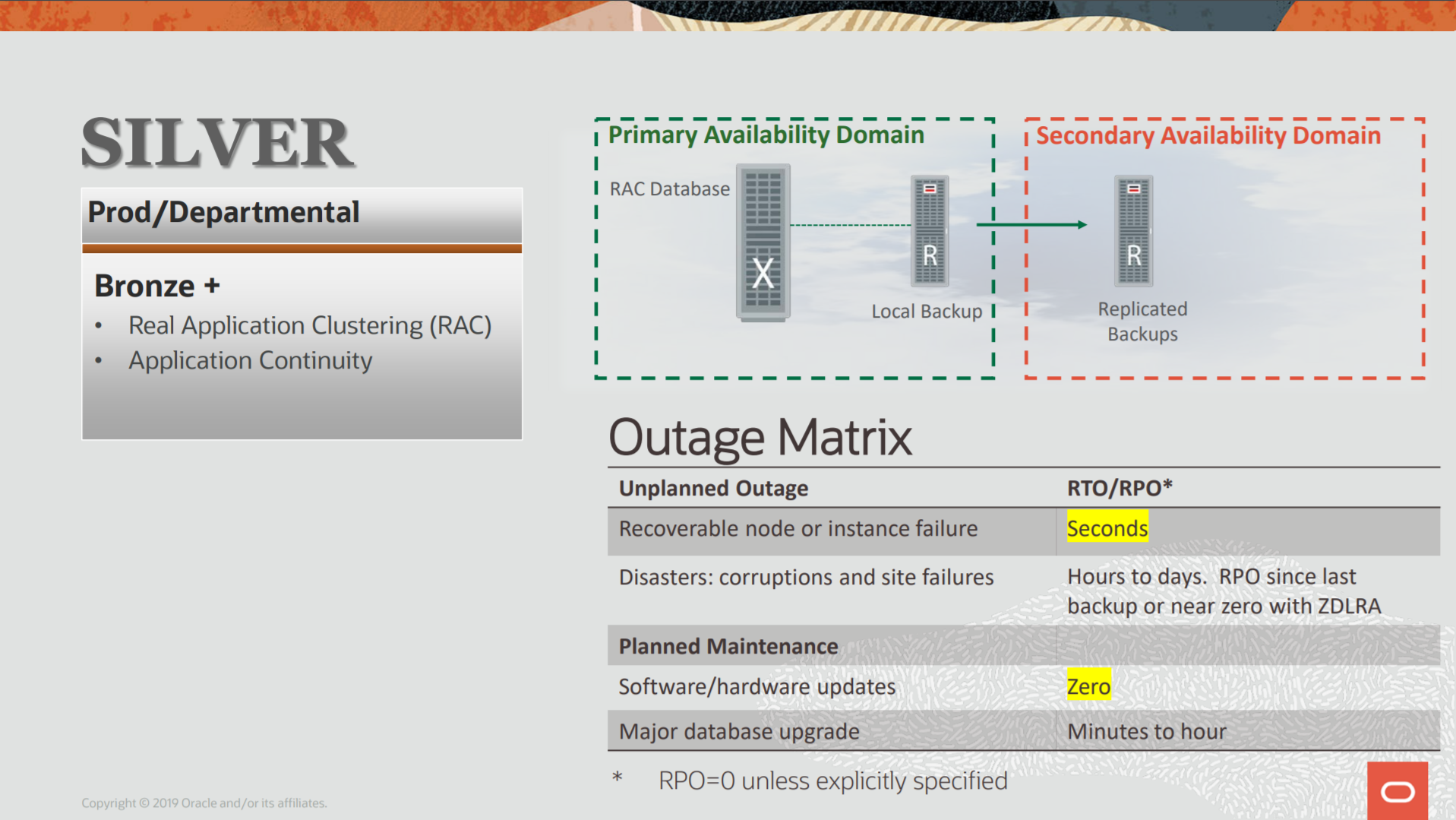 As you can see above, the Silver by MAA blueprints improves compared with Bronze architecture that I spoke at the last post. But the basic points are there: RPO and RTO. They continue to base rule here. And the goals are the same: Data Availability, Data Protection, Performance (no impact), Cost (lower cost), and Risk (reduce). More technical details here at the MAA Overview doc.
As you can see above, the Silver by MAA blueprints improves compared with Bronze architecture that I spoke at the last post. But the basic points are there: RPO and RTO. They continue to base rule here. And the goals are the same: Data Availability, Data Protection, Performance (no impact), Cost (lower cost), and Risk (reduce). More technical details here at the MAA Overview doc.